After I migrated from pfSense to OPNSense for my firewall embedded within a Proxmox lab, I was stumped for two days looking for this obscure setting. It was a problem right out of the box: After I got the interfaces configured and assigned static IPs for the two network interfaces, I tried and tried to gain access to the Web UI using the WAN interface. It worked great from the LAN interface, but was invisible to WAN.
You may already know it is not a good practice to access a firewall from its WAN interface. That is true, unless you're using the firewall's WAN interface to connect to your local LAN, not the public internet. This happens, for example, when you are running the firewall on a virtual machine inside Proxmox, which is all happening behind an internet router.
So when you search for keywords in the headline above: "OPNSense, Web UI, Proxmox, WAN, fail" you'll find plenty of people telling you not to do what I'm about to tell you to do. But their advice does not fix the problem I was facing, which was buried in an obscure "reply-to" setting I'll explain shortly.
To summarize what the search engines will tell you: It is bad practice to access OPNSense via its WAN network interface when it is set up like this:
INTERNET --> (WAN)-OPNSENSE-(LAN) --> Physical Machines
This is because you're giving direct access to your firewall to the Internet. However, this is acceptible:
INTERNET --> (WAN)-ROUTER-(LAN) -- dedicated LAN IP --> [(WAN)-OPNSENSE-(LAN) --> Virtual Machines]
(Proxmox is the part within the square brackets). This way, no one can get to your OPNSense firewall from the Internet, since they could never have your dedicated LAN SRC IPAddress, such as 192.168.10.12, since that SRC requires them to be inside your internal network.
So I configured things this way. And it wouldn't work. It wouldn't work. It wouldn't work. Looked into logs. I looked everywhere. Uninstalled, reinstalled, looked into logs more. There, I found the most curious thing: the packet was arriving at the firewall, getting passed in as my rules allowed, and NOTHING. No response, no failure, just a complete dead end, as if traffic were not getting through the firewall, even though logs showed it clearly was! I searched the Internet for this problem, but because I was missing the key search term ("reply-to", I never found the solution until I finally got to the point where I started toggling config settings that looked suspicious. I finally found this one:
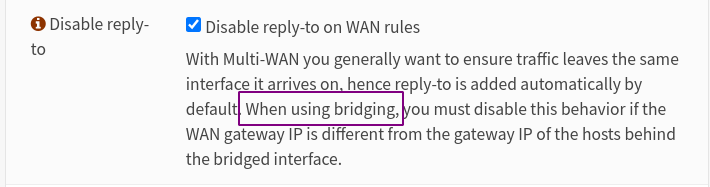
I'm using bridging, so I toggled this off, and suddenly my Web UI appeared! Hooray!
So WTF is reply-to on WAN?
I researched this obscure setting a little. It is well-debated. Others agree it shouldn't be used as a default setting, but it's been around for years, which means changing it causes problems for people used to it the way it is, so it looks like it won't be changed any time soon. Which means others will encounter this same problem.
So for others using search engines I'm making this blog post with a specific SEO-friendly headline in order to link together the keywords "OPNSense, Web UI, Proxmox, WAN, fail" with the keyword "reply-to" so you people can solve this issue faster when it appears.
Here is the setting in its full context (Firewall, Settings, Advanced, Disable reply-to), if you found this post helpful.